Introduction
Modern teams love how fast the cloud lets them move. But every new account, VPC, database and container also opens a new way for attackers to get in.
If you are responsible for Cloud Infrastructure, you probably ask yourself the same questions over and over.
- Are our environments really locked down?
- Could a simple misconfiguration expose customer data?
- Would we notice if someone was already inside?
This guide walks through those questions one by one and turns them into a practical approach you can apply in AWS or any major cloud platform.
Cloud providers handle physical data centers, hardware and core networking, but you are still responsible for how your Cloud Infrastructure is configured, who can access it, and how data is protected. This is the essence of the shared responsibility model used by AWS and other major providers.

Why Is Securing Cloud Infrastructure So Hard For Teams Today?
The problem is not that cloud is insecure. The problem is that cloud is extremely configurable.
Common reasons teams struggle:
-
Multiple accounts and projects with different standards.
-
Fast moving dev teams creating resources outside any security review.
-
Manual, one off changes instead of security as code.
-
Confusion about what is the provider’s responsibility and what is yours.
Without a clear model, security becomes a collection of tools, not a system. The rest of this guide focuses on building that system
How Do You Design A Secure Landing Zone From Day One?
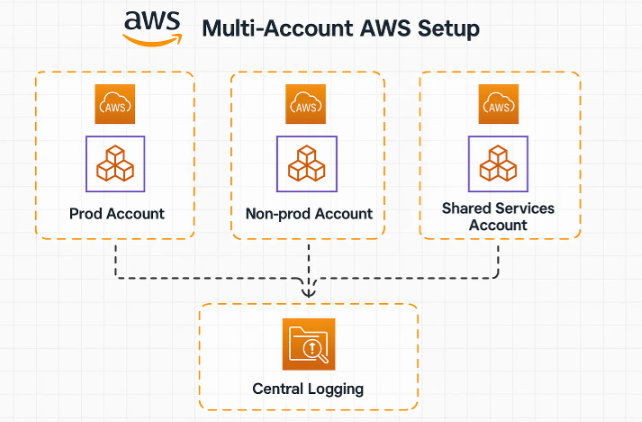
A cloud landing zone is the structural backbone of your entire cloud environment, defining how accounts, networks, and guardrails are established before any workload goes live. A secure one isolates environments into separate accounts to contain blast radius, standardizes all networking decisions up front (VPCs, subnets, CIDRs, public vs private services), centralizes all audit and flow logs into a dedicated logging account for monitoring
How Should You Manage Identity And Access In The Cloud?
Cloud security failures almost always tie back to identity misuse — stolen credentials, excessive permissions, or forgotten keys — so a solid identity strategy is non-negotiable. Centralize authentication through a single corporate identity provider with MFA, enforce role-based access built around job functions, and apply strict least-privilege policies instead of lazy admin-level access. Sensitive actions should rely on short-lived, JIT permissions with approval flows, while long-term system access should use assumable roles rather than hardcoded keys to eliminate secret leakage risks.
How Should You Manage Identity And Access In The Cloud?
Cloud incidents overwhelmingly stem from identity failures — stolen credentials, excessive permissions, or stagnant keys — so identity must be engineered, not improvised. Centralize sign-in through a single corporate identity provider with MFA, enforce role-based access tied to job functions (not individuals), and practice strict least privilege instead of handing out admin rights for convenience. Sensitive actions should use short-lived, approved elevation, while long-term workload access should rely on assumable roles rather than hardcoded keys to eliminate secret-leak risks.
How Can You Protect Data At Rest And In Transit?
Your Cloud Infrastructure may be highly distributed, but attackers care most about one thing: your data. Protecting it has two parts.
Encryption At Rest
Make encryption at rest the default for all data stores. Modern cloud storage, block volumes and managed databases support built in encryption with customer managed keys.
Where possible:
-
Use a centralized key management service rather than application level ad hoc encryption.
-
Segment keys by environment and sensitivity.
-
Limit who can administer keys and who can use them to encrypt or decrypt.
Encryption In Transit
Enforce TLS for all client and service connections. Use modern cipher suites and disallow plain HTTP access for public endpoints. For internal services, use service meshes or load balancers that terminate TLS in a controlled way.
Data Classification And Access Controls
Not all data is equal. Classify data as public, internal, confidential and restricted. Map these classes to concrete controls in your Cloud Infrastructure such as:
-
Allowed storage services.
-
Network exposure rules.
-
Backup and retention requirements.
When these patterns are defined centrally, new projects can move faster without redesigning data protection each time.
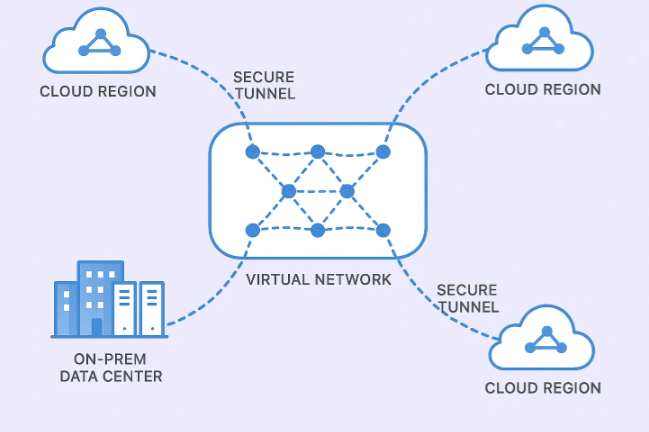
How Do You Secure Cloud Networks And Hybrid Connectivity?
Networking is where many Cloud Infrastructure security issues quietly appear. An extra open port here, a misconfigured route there, and suddenly a private system is reachable from the internet.
Core practices for network security:
Use Private Subnets For Critical Services
Keep databases, internal APIs and batch systems in private subnets without direct internet access. Use NAT gateways or proxies for outbound traffic, and load balancers or API gateways for controlled inbound traffic.
Segment By Environment And Sensitivity
Do not flatten your entire Cloud Infrastructure into one large network. Separate VPCs or virtual networks by environment, and use peering or transit hubs with explicit routing.
Secure Hybrid Links
If you connect to on prem through VPNs or direct connections, treat that as a high value path. Use strong authentication, limit the routes that are shared, and monitor traffic.
Control Egress
Many breaches involve data being exfiltrated to external destinations. Consider using egress filters or firewalls that restrict which domains or IP ranges workloads can talk to.
When your network layout is intentional and documented, troubleshooting security issues also becomes easier.
How Do You Keep Servers, Containers And Serverless Workloads Safe?
Cloud Infrastructure compute is now a mix of virtual machines, containers and serverless functions. Each has slightly different security needs, but the goals are the same: minimize attack surface and keep runtimes patched.
For virtual machines:
-
Use golden images or templates that already include hardening, logging agents and security tools.
-
Automate patching windows, especially for exposed bastion hosts and web servers.
For containers:
-
Scan base images in a registry before deploying.
-
Drop unnecessary capabilities and run containers as non root where possible.
-
Limit network and storage access for each workload.
For serverless:
-
Review permissions attached to functions. They often start with wide permissions that never get tightened.
-
Monitor cold starts and timeouts for unusual behavior, which can indicate misconfigurations or abuse.
Which Monitoring, Logging And Threat Detection Do You Really Need?
You cannot secure Cloud Infrastructure you cannot see. The challenge is doing monitoring in a way that is both comprehensive and usable.
You usually need three layers:
Foundational Logging
Enable audit logs for every account and region. This includes activities such as API calls, console logins and configuration changes. Route these logs into a central store.
Operational Observability
Collect metrics, logs and traces from applications and infrastructure. Use them for both performance and security insight. Error spikes, latency jumps or memory issues can be early signs of attacks.
Threat Detection And Alerting
Use managed threat detection services and rules that look for known bad patterns such as unusual API calls, new public S3 buckets, or suspicious network flows. Datadog
Start with a small, carefully chosen set of alerts that your team can realistically respond to. Refine over time. Too many alerts create noise and hide real incidents.
How Can You Align Cloud Infrastructure Security With Compliance?
If you operate in regulated sectors like banking, public sector or healthcare, you must align Cloud Infrastructure security with formal frameworks and local regulations.
A useful mental model is:
-
Regulations define outcomes.
For example, log retention, data residency, incident response expectations. -
Your cloud platform provides building blocks.
Accounts, regions, encryption options, logging services, identity and access tools. -
Your architecture connects the two.
Create a simple control matrix that maps each requirement to a specific technical control in your Cloud Infrastructure, such as:
-
All customer data is stored in approved regions only.
-
All production databases are encrypted with customer managed keys.
-
All admin actions are logged and reviewed regularly.
-
Disaster recovery is tested against agreed recovery time and recovery point objectives.
This mapping not only helps you pass audits, it also makes security conversations with business stakeholders much clearer.
Conclusion
Security is not a one time project. Cloud platforms, services and threats evolve constantly. To keep your Cloud Infrastructure secure in a sustainable way:
-
Treat security controls as products that you iterate on.
-
Keep infrastructure definitions in version control and review them like application code.
-
Run regular game days where you simulate incidents and test runbooks.
-
Keep business stakeholders involved so security decisions align with real risks and priorities.
When security, platform and application teams share the same view of Cloud Infrastructure, you remove the gaps where attackers usually hide.
Done well, security does not slow you down. It gives your teams more confidence to experiment, scale into new regions and adopt new services, knowing there is a clear, tested guardrail system underneath.